Metasploit install ,run
-
Install & build https://github.com/rapid7/metasploit-framework
$ git clone https://github.com/rapid7/metasploit-framework.git
$ cd ./metasploit-framework
$ docker-compose build
-
run
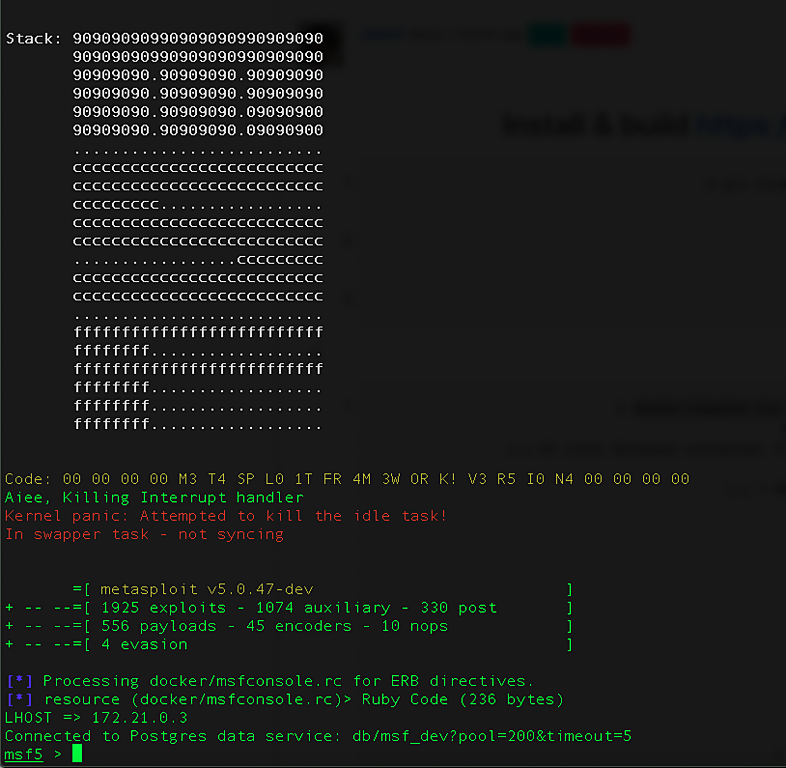
$ docker-compose run --rm --service-ports -e MSF_UID=$(id -u) -e MSF_GID=$(id -g) ms Creating metasploit-framework_db_1 ... done [-] No local database connected. Please connect to a local database before connecting to a remote data service. [-] *** [-] * WARNING: No database support: No database YAML file [-] *** # cowsay++ ____________ < metasploit > ------------ \ ,__, \ (oo)____ (__) )\ ||--|| * =[ metasploit v5.0.47-dev ] + -- --=[ 1925 exploits - 1074 auxiliary - 330 post ] + -- --=[ 556 payloads - 45 encoders - 10 nops ] + -- --=[ 4 evasion ] [*] Processing docker/msfconsole.rc for ERB directives. [*] resource (docker/msfconsole.rc)> Ruby Code (236 bytes) LHOST => 172.21.0.3 Connected to Postgres data service: db/msf_dev?pool=200&timeout=5
-
how to use scanner http auxiliary modules https://www.offensive-security.com/metasploit-unleashed/scanner-http-auxiliary-modules/
msf5 > db_status [*] Connected to msf_dev?pool=200&timeout=5. Connection type: postgresql. Connection name: HrN4ljHU. msf5 > use auxiliary/scanner/http/cert msf5 auxiliary(scanner/http/cert) > show options Module options (auxiliary/scanner/http/cert): Name Current Setting Required Description ---- --------------- -------- ----------- ISSUER .* yes Show a warning if the Issuer doesn't match this regex RHOSTS yes The target address range or CIDR identifier RPORT 443 yes The target port (TCP) SHOWALL false no Show all certificates (issuer,time) regardless of match THREADS 1 yes The number of concurrent threads msf5 auxiliary(scanner/http/cert) > set RHOSTS 192.168.1.0/200 <--- 200 may be CIDR must be 8bit value (8,16,24,32) RHOSTS => 192.168.1.0/200 msf5 auxiliary(scanner/http/cert) > run [-] Auxiliary failed: Msf::OptionValidateError The following options failed to validate: RHOSTS. msf5 auxiliary(scanner/http/cert) > set RHOSTS 192.168.1.0/24 RHOSTS => 192.168.1.0/24 msf5 auxiliary(scanner/http/cert) > set THREADS 254 THREADS => 254 msf5 auxiliary(scanner/http/cert) > run [+] 192.168.1.221:443 - 192.168.1.221 - '0.0.0.0' : '2015-12-21 16:44:45 UTC' - '2016-12-20 16:44:45 UTC' (EXPIRED)' [*] 192.168.1.0/24:443 - Scanned 39 of 256 hosts (15% complete) [*] 192.168.1.0/24:443 - Scanned 72 of 256 hosts (28% complete) [*] 192.168.1.0/24:443 - Scanned 124 of 256 hosts (48% complete) [*] 192.168.1.0/24:443 - Scanned 255 of 256 hosts (99% complete) [*] 192.168.1.0/24:443 - Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed
## Must be changing 192.168.0.100, 192.168.0.1 to your target IP ## Must be changing www.yoursite.com to your target DOMAIN use auxiliary/scanner/http/cert set RHOSTS 192.168.0.1/24 set THREADS 100 run use auxiliary/scanner/http/dir_listing set RHOSTS 192.168.0.100 set THREADS 50 run use auxiliary/scanner/http/dir_scanner set RHOSTS 192.168.0.100 set THREADS 50 run use auxiliary/scanner/http/dir_webdav_unicode_bypass set RHOSTS 192.168.0.1/24 set THREADS 100 run use auxiliary/scanner/http/enum_wayback set DOMAIN www.yoursite.com set THREADS 11 run use auxiliary/scanner/http/files_dir set RHOSTS 192.168.0.100 set THREADS 11 run use auxiliary/scanner/http/open_proxy set RHOSTS 192.168.0.100 set THREADS 11 run use auxiliary/scanner/http/options set RHOSTS 192.168.0.100 set THREADS 11 run use auxiliary/scanner/http/robots_txt set RHOSTS 192.168.0.100 set THREADS 11 run use auxiliary/scanner/http/ssl set RHOSTS 192.168.0.100 set THREADS 11 use auxiliary/scanner/http/http_version set RHOSTS 192.168.0.100 set THREADS 11 run use auxiliary/scanner/http/webdav_scanner set RHOSTS 192.168.0.100 set THREADS 11 run use auxiliary/scanner/http/webdav_website_content set RHOSTS 192.168.0.100 set THREADS 11 run